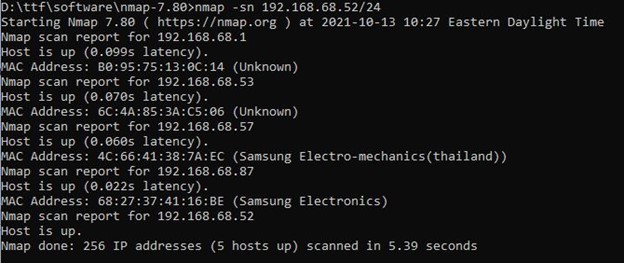
In this article, I use nmap, a popular utility, to illustrate a simple example.
For those familiar with my work, I always mention that you should 'know your tools,' so I won't beat that point to death. I have plenty of examples on my website in case you are new to my work.
When you use the -sn subnet option in nmap, the help screen mention that it is a "Ping Scan." Most analysts know ping and probably know that ping uses ICMP as its protocol. Well, in this video, you will see how I used Wireshark to observe how nmap discovers a subnet and if it uses ICMP to accomplish this.
With this specific option on Windows 10, the utility uses ARP for its discovery mechanism.
When you think about it, ARP is a much better protocol to use since ICMP could be rerouted, blocked, or response spoofed. After you figure out your tool behavior, understanding how it behaves on your network and devices becomes obvious.
I encourage you to spend a few minutes with your favorite troubleshooting tools to figure out how they behave. Don’t forget to retest your favorite software with devices and networks you are familiar with whenever a new version comes out to ensure the tool still reports the results the same way and that behavior hasn’t changed.
See other hands-on tool reviews by Tony Fortunato here.