While installing a new Cisco router for a client recently, I was a bit surprised that there was no firewall. I asked if the router was configured with some of the basic security settings to keep curious eyes from prying. The client’s IT administrators said they hadn’t thought of it and weren’t too concerned. When they showed me the router configuration, all sorts of red flags went up. I tried to figure out how to make them understand how vulnerable the lack of Cisco security precautions made the organization and how to fix the problem.
I suggested that since this router won’t be live for a few more days, let’s conduct an experiment. I would use a couple of basic Cisco IOS configuration commands to somewhat secure the routers and we would review the logs in the morning. Specifically, I used the Cisco Login Block feature, which essentially blocks your IP address if there are a specified number of incorrect login attempts. I then used a free syslogger and configured the router to log all events to our computer so we could better sort and filter out any events that were reported over the evening.
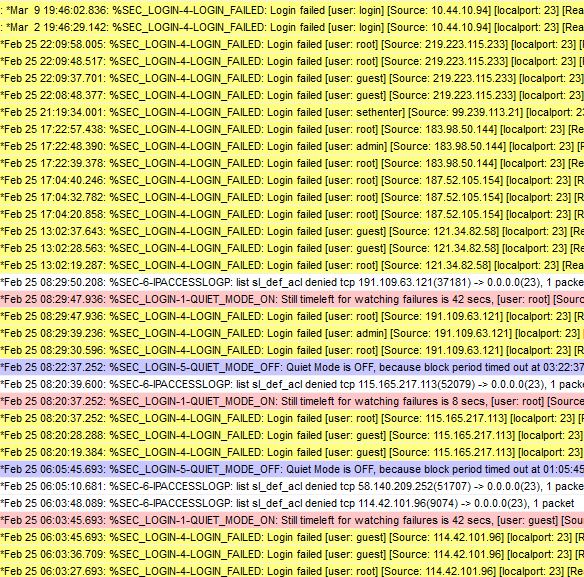
As you can see below, there were a lot of curious eyes poking around the router. (The 10.44.10.94 at the top was us testing.)
After the IT admins saw the log, they were convinced and agreed that the router should have some basic protection.
I understand this site is one of many small remote offices the client supports and the time and money required to put a firewall at every location would not be feasible. Even if they had the money and equipment, that kind of protection would take an extremely long time to implement. However, router configuration changes are easy to make remotely and in an automated fashion.
So here are some of the basic steps that I think you should consider when configuring a Cisco device facing an untrusted network, assuming you may need these protocols on the interior:
- Disable or block Telnet or SSH
- Use Cisco Login Block
- Disable or block SNMP
From the interior side of the device:
- Centralize log collection and monitoring
- Make sure your secret and username passwords are encrypted in your configuration
- Disable unused services
- Limit access with ACLs
- Use encrypted protocols like HTTPS and SSH
This would be the minimum configuration for Cisco devices. Most of these tips can be applied to non-Cisco routers as well, but and you should always consult your vendor to see if it has more specific information. Moreover, Cisco has a lot of documentation for hardening your IOS devices.
At my client’s site, after configuring the router, we remotely tried pinging, Telnetting/SSH and using HTTPS to prove that the router won’t respond to the requests. With the syslog server collecting events, the IT team has a way to monitor the router and enjoy some peace of mind that the more obvious hacking techniques will not work with the router.
Learn more about protecting your IT infrastructure in the Security Track at Interop Las Vegas this spring. Don't miss out! Register now for Interop, May 2-6, and receive $200 off.